With the release of ONTAP 9.10.1 comes a new feature built into ONTAP, anti-ransomware detection.
What it Does
One of the concerns of a ransomware attack is the lack of visibility, which directly impacts response time. If ransomware kicks off overnight, or over the weekend it could be hour or days before anyone knows what happens. For archive environments it could be even longer with disastrous consequences.
Anti-ransomware detection in ONTAP is built on file system analytics and uses “machine learning” to detect possible ransomware attacks on NAS. The first thing it’s looking for is whether the incoming data is “encrypted or plaintext.” It then looks for, and I quote,
- High data entropy* (an evaluation of the randomness of data in a file)
- A surge in abnormal volume activity with data encryption
- An extension that does not conform to the normal extension type
*Emphasis directly from the documentation.
When ransomware is detected it automatically takes a snapshot of the suspect volume. Thus, if if a ransomware attack takes place, a prompt snapshot can help your RPO by quickly returning to a good known state. Plus, with the speed of a native restore, you’ll have the best available RTO.
For more information on this I recommend this video from NetApp’s 2021 Insight catalog (BRK-1074-2 Fight Ransomware: The NetApp ONTAP Solution in 2021).
Requirements
Ransomware detection only works for NAS services running natively on ONTAP. If you’re running those shares in a Windows virtual machine, no dice.
From a licensing perspective you need the Security and Compliance license bundle. That’s the one that comes with SnapLock and multi-tenant key management.
The boffins at NetApp marketing are trying to figure out what they want to rename the “Security and Compliance” software bundle to.
How to Enable It
Enabling anti-ransomware protection is easy – even easier than creating a volume and choosing an aggregate at creation.
Simple go into your volumes view, click the three dots next to the volume, and then select “Enable Anti-ransomware.”
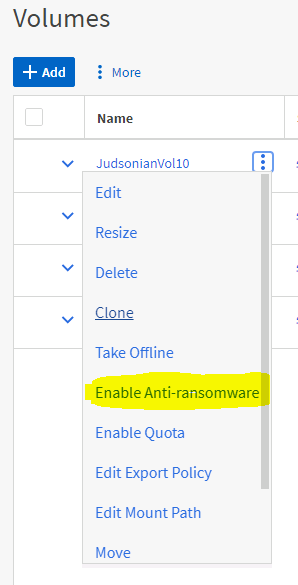
Once you enable the feature the volume will enter a learning mode. During this period ONTAP will begin capturing analytics regarding user behavior on the selected volume. The recommendation is to let this run for 7 to 30 days before enabling the actual service. You can enable the feature at anytime, no need to wait for the recommended 7 days.
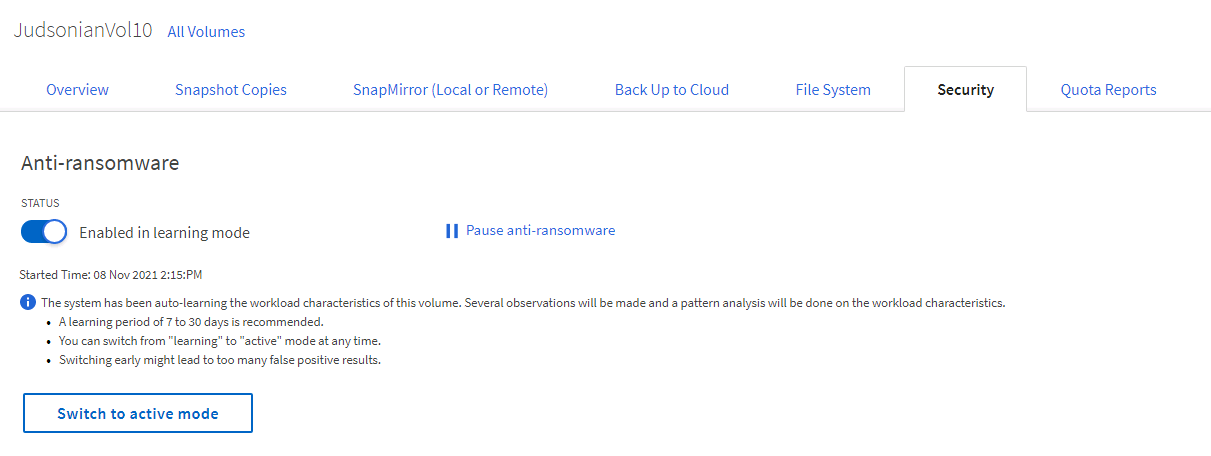
What happens when an attack is detected?
Sooooo… I don’t know how to safely get some ransomware to test out in my lab environment. Instead I’m just going to post some low quality screenshots from that aforementioned Insight session.
When anti-ransomware detection is enabled you’ll get a warning in the volume saying there’s abnormal volume behavior, the date of the detection, and the files that the system things are potential ransomware.
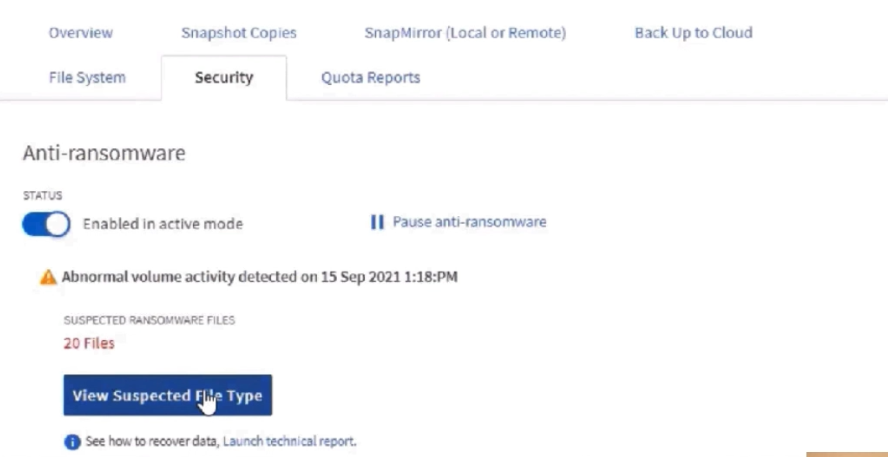
You can then click and view the suspected file types for quick visibility on what was tagged.
When a potential attack is detected the snapshot that’s created will be named Anti_ransomware_backup.[date]. This makes it very easy to identify your best restore point.
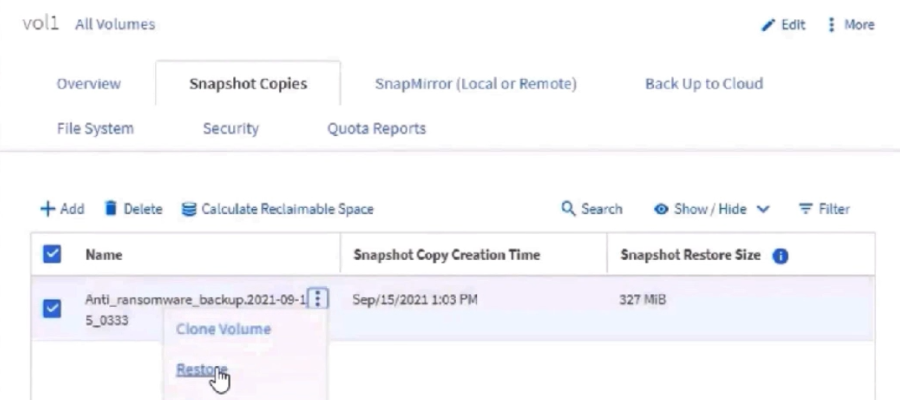
One thing I haven’t seen is whether or not any notifications are pushed to the front page of System Manager. If you want more real time alerting, check out EMS or Cloud Secure, more on that below.
Via Command Line
There’s also new command line functionality that does the above.
Everything is under > security anti-ransomware and the line structure is consistent with the rest of ONTAP CLI. Some examples…
View status on a volume…
judsonian::> security anti-ransomware volume show -vserver [SVM name] -volume [volume name] Vserver Name: [SVM name] Volume Name: [volume name] State: enabled Attack Probability: none Attack Timeline: [if there's a potential attack, the time will be here] Number of Attacks: -
You can check detection status of a volume by running…
judsonian::> security anti-ransomware volume workload-behavior show -vserver [SVM name] -volume [volume name] Vserver : [SVM name] Volume : [volume name] File Extensions Included : [this will list all the file types in that volume]
When an attack is detected you can use this command to view the impacted files…
judsonian::> security anti-ransomware volume attack generate-report -vserver [SVM name] -volume [volume name] -dest-path [SVM name]:[volume name]/ Report "report_file_[SVM name]_[volume name]_[date]" available at path "[SVM name]:[volume name]/"
A text file will show up in the destination provided with a list of files, paths, and dates.
And this command to see which snapshot was taken automatically…
judsonian::> snapshot list -vserver [SVM name] -volume [volume name] Vserver Volume Snapshot Size Total% Used% ---------- ------------- -------------------------------------- ------- ------ ----- [SVM name] [volume name] Anti_ransomware_backup.[snapshot date] 1582KB 0% 0%
If there’s any files that are generating a false positive, such as ones intentionally being encrypted by an application, you can clear them of suspicion…
judsonian::> security anti-ransomware volume attack clear-suspect -vserver [SVM name] -volume [volume name] -false-positive true -extensions mp3 Suspect records cleared: 42.
You can’t preemptively set cleared extensions, I tried.
Limitations
As this is the first public iteration of this feature there are some important limitations.
Here’s the list from the official documentation (minus a typo).
Unsupported system configurations:
- SAN environments
- ONTAP S3 environments
- VMDKs on NFS
- Cloud Volumes ONTAP
- Cloud Volume Services for AWS and Google Cloud
- Azure NetApp Files
- Amazon FSx for ONTAP
Unsupported volume types:
- offline volumes
- restricted volumes
- SnapLock volumes
- FlexGroup volumes
- FlexCache volumes
- SAN-only volumes
- volumes of stopped storage VMs
- root volumes of storage VMs
- data protection volumes
Emphasis mine.
Most of those are pretty straight forward and expected. SnapLock and FlexGroup I hope will get support soon. The latter because it’s popularity and flexibility, where SnapLock is a key feature of the license bundle this is a part of. SnapLock limitations make sense in a certain respect too, since the software is designed to limit the removal of snapshots and I imagine anti-ransomware has the potential create more snapshots than may be necessary in a preventative/protective way.
How does this compare to Cloud Secure?
Cloud Secure has more advanced features compared to this within-ONTAP solution. For starters, it has a much easier to use GUI that provides even more information like the user account suspected of participating in the attack. You can also set up email alerts directly through Cloud Secure. Alerting might be possible natively from Unified Manager 9.10, but I need to check in on that. Locally, ONTAP’s alerting will send up an ASUP (which, I suppose you can get directed to yourself as well) along with EMS logging.
If you have an environment with multiple clusters, Cloud Secure comes across as the better option since it can pull in from multiple sources and present on all of them in a single environment. Cloud Secure can also alert on other suspicious behavior, like users accessing files they shouldn’t.
The last consideration is cost. Cloud Secure has a retail cost of $9 per 4 TiB of raw capacity being monitored. Oh, and you get the awesomeness that is Cloud Insights for that covered capacity as well. ONTAP anti-ransomware detection requires the Security and Compliance bundle – not clue on how that pricing works.
Additional Information
- Anti-Ransomware Overview (the official documentation)
- BRK-1074-2 Fight Ransomware: The NetApp ONTAP Solution in 2021 (Insight 2021 session that covers this as a new feature within ONTAP)
- Prevent ransomware spread with ONTAP automatic ransomware protection (a blog post on the feature
Article History
- 11/9/2021 – Initial Posting
- 11/11/2021 – Added section on limitations
